According to other vendors, your options are now limited. Even if you do get an extraction, it will only acquire basic information. BFU means the data is encrypted and secured.
Fear not, XRY and XRY Pro can still acquire a decrypted FFS or physical from a device in BFU – if it is supported, of course.
Is this magic? Not at all. Vendors have advertised what is limited about their BFU extractions but that is not the case for every player in the industry. Unfortunately, this scenario is now leaving examiners with the conclusion that all BFU extractions only produce limited data. And that is simply not true.
One thing that is often overlooked, especially when it comes to processing Android devices is that not only should you consider the make of the device, but you should also consider the chipset of the device. Most exploits from vendors will be against a specific chipset. So, success or failure can be determined prior to commencing the extraction by doing your homework.
There is another way, enter XRY and XRY Pro:
Troubled by an MTK device? MSAB has BFU support for those. Frustrated with a device containing a UNISOC chipset? You guessed it, we have BFU support for that too. We cover Samsung, LG, Motorola, OnePlus, Sony, Vivo, Xiaomi, Pixel, and Huawei, plus others. Of course, it comes with the favorite caveat within the DFIR industry – it depends! Check your chipset, do your homework and you will be on the right track for a successful extraction. XRY Pro offers support for FDE, FBE and Secure Startup.
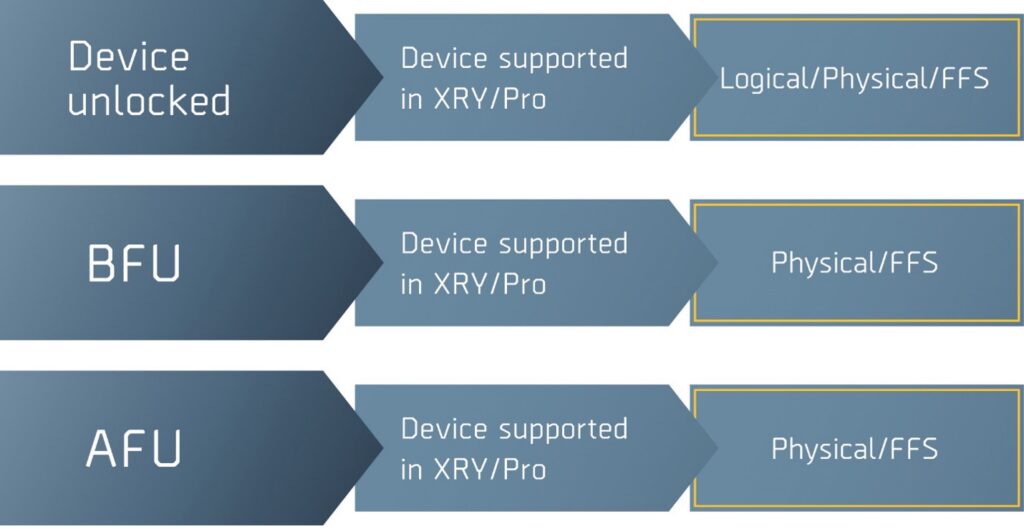
But they say it will only produce limited results:
Hopefully, this post will help alleviate fears of a limited extraction when you find a device in a BFU state. Terms such as FFS, AFU and BFU are accepted terminology for this industry; however, the output from each state is not.
As we are all aware, this industry does not stand still and as a vendor, MSAB must adapt our methods to help you continue to have access to the latest mobile devices. Here at MSAB we don’t want you to think that your case can’t be progressed, especially if your decision-making is based on a statement from another vendor. Always explore your options and your tools and exhaust all avenues before you place that mobile device back on the shelf unprocessed.
There is a reason that it is recommended to have multiple tools. Validation, of course, is the most important motivation, but access to devices is another crucial factor.
So, the next time you come across a device that is in BFU state, make sure that you double click on XRY.
MSAB – your trusted partner in digital forensics.
Terminology
| Term | Definition |
| AFU | After first unlock. A state where the device has been unlocked at least one time since it was last turned on. |
| BFU | Before first unlock. A state where the device has rebooted or powered on and not been unlocked since the reboot/power on. |
| DEK | Data encryption key |
| FBE | File based encryption. Devices running Android 7 and higher can support file-based encryption whereby every different file is encrypted with a different key independently. Modern devices come with such encryption by default. |
| FDE | Full disk encryption, former encryption method for older Androids. |
| Secure startup | Secure startup protects the device by requiring a password or PIN each time the device is turned on |
| FFS | Full File System Extraction |
[Partner content]




